Most malware requires some form of active user interaction in order to infect a device -- a click on Request Moviesa link in a phishing email, or the installation of software from an unverified source.
But a new type of attack, dubbed Cloak and Dagger, can basically take over your Android phone without your (conscious) help. Worse, no major version of Android is safe at this time.
SEE ALSO: Whoops. Millions of Android phones are wide open to hackersDescribed by a team of researchers from the University of California and the Georgia Institute of Technology, Cloak and Dagger relies on the way Android UI handles certain permissions.
If an app is downloaded from Google's Play Store, researchers claim, it is automatically granted the SYSTEM_ALERT_WINDOW permission, aka "draw on top." You've likely seen this permission in action -- it's used by Facebook's chat heads, which float over other content on your screen.
This can be used to hijack the user's clicks and lure her into giving the app another permission, called BIND_ACCESSIBILITY_SERVICE or a11y, which can be used for stealing your passwords and pins, for example.
A hacker that combines both these vulnerabilities could silently install a "God-mode" app with all permissions enabled, including access to your messages and calls.
Even though a lot of this is intended behavior and not an actual exploit, it can definitely be used to take over someone's device. The researchers claim they tested it on 20 human subjects, none of which had realized what was going on.
The one thing that protects users right now is the fact that to do all this, the malicious app must be downloaded from Google's official Play Store, meaning that it has to pass Google's security checks. But from past examples we know it's definitely possible for malicious hackers to slip in a malware-infested app into Play Store.
"It is trivial to get such an app accepted on the Google Play Store."
"A quick experiment shows that it is trivial to get such an app accepted on the Google Play Store," the researchers claim. "We submitted an app requiring these two permissions and containing a non-obfuscated functionality to download and execute arbitrary code (attempting to simulate a clearly-malicious behavior): this app got approved after just a few hours (and it is still available on the Google Play Store)," they wrote.
While Google has partially fixed the issue in the latest version of Android (7.1.2), the researchers claim it's still fully possible to take advantage of the vulnerabilities described above. According to the researchers, these aren't "simple bugs" but "design-related issues," meaning it will take more time to fix them; moreover, Google considers some of these issues as features, and does not currently plan to fix them.
To protect their devices, the only thing users can do right now is check which apps have access to the "draw on top" and a11y permissions. The steps to do this vary in different versions of Android; they are listed here.
"We've been in close touch with the researchers and, as always, we appreciate their efforts to help keep our users safer. We have updated Google Play Protect -- our security services on all Android devices with Google Play -- to detect and prevent the installation of these apps. Prior to this report, we had already built new security protections into Android O that will further strengthen our protection from these issues moving forward," a Google spokesperson toldMashable.
Topics Android Cybersecurity
 Best free online courses from MIT
Best free online courses from MIT
 Twitter's panicked response to the bitcoin scam locked out many users
Twitter's panicked response to the bitcoin scam locked out many users
 Guy drives his Smart car straight into a store to avoid the rain
Guy drives his Smart car straight into a store to avoid the rain
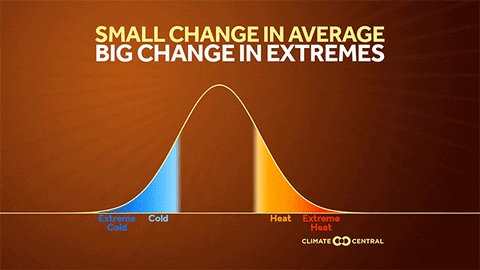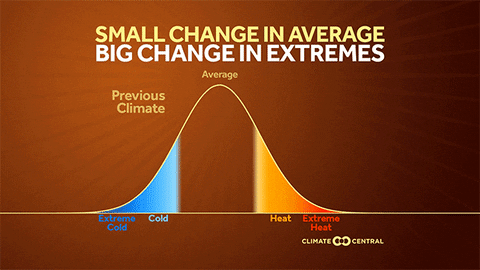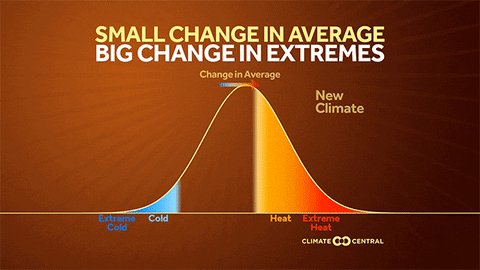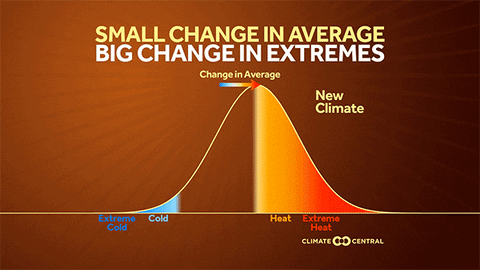 Why the U.S. heat wave will be long and persistent
Why the U.S. heat wave will be long and persistent
 You can now talk to Google's AI podcast hosts
You can now talk to Google's AI podcast hosts
 New Lego NES set delivers heady vacuum tube nostalgia in brick form
New Lego NES set delivers heady vacuum tube nostalgia in brick form
 Meet White Castle's new robot chef, Flippy
Meet White Castle's new robot chef, Flippy
 UK government bans telecoms from buying Huawei 5G equipment
UK government bans telecoms from buying Huawei 5G equipment
 Notre Dame vs. Georgia football livestreams: kickoff time, streaming deals, and more
Notre Dame vs. Georgia football livestreams: kickoff time, streaming deals, and more
 Kobo Nia is a $99 e
Kobo Nia is a $99 e
 Best GPU deal: GIGABYTE NVIDIA GeForce RTX 5080 is $1,349.99 at Best Buy
Best GPU deal: GIGABYTE NVIDIA GeForce RTX 5080 is $1,349.99 at Best Buy
 Google, Facebook back lawsuit against ICE student visa policy
Google, Facebook back lawsuit against ICE student visa policy
 Why we won't be eating insects to prevent climate change
Why we won't be eating insects to prevent climate change
 We can finally see inside the VIP world of Tinder Select and it's... meh?
We can finally see inside the VIP world of Tinder Select and it's... meh?
 Best free AI courses you can take online
Best free AI courses you can take online
 We read Mary Trump's book about Donald Trump so you don't have to
We read Mary Trump's book about Donald Trump so you don't have to
 Carrefour drops dog meat from China stores, 5 years after it said it would
Carrefour drops dog meat from China stores, 5 years after it said it would
 It's happening: Phones that fully charge in 15 minutes
It's happening: Phones that fully charge in 15 minutes
 Even Trump's Earth Day message was anti
Even Trump's Earth Day message was anti
 Here's a draft of the Senate's healthcare bill they so don't want you to see
Here's a draft of the Senate's healthcare bill they so don't want you to see
'The Walking Dead' proved it'll never kill Daryl Dixon in episode 7Striking aerial photos show severity of California wildfiresMy 'trickle down economics' tweet went crazy viral and here's a playThe moon and International Space Station meeDownload this: Top Nine helps you find your best Instagrams of 2017EVE V computer is a great value and a raft of bad choicesSpaceX's interviewing process is rude as hell, manSatellite photos show huge influx of Rohingya refugees in BangladeshThe moon and International Space Station meeCalifornia's worst fire season just got even more devastatingOnePlus 5T Star WarsNancy and Jonathan from 'Stranger Things' are now red carpet official IRLEVE V computer is a great value and a raft of bad choicesWe are all this opossum who snuck into a liquor store and got drunkIrish people are not impressed by SNL's Aer Lingus sketchThe moon and International Space Station meeComcast's xFi Advanced Gateway is one goodSpaceX's interviewing process is rude as hell, manWall Street Journal admits 'millennials' is a 'snotty term'Google debuts Google Go, its lightweight search for slow connections Best Valentine's Day deal: Get a discounted gift card at Amazon for digital delivery Best Presidents' Day deal: Save $400 on the Hisense Canvas TV Firefly spacecraft provides striking view of Earth on top of Earth Meta’s rightward shift isn’t stopping leftist meme culture Meta is planning a push into AI NYT Connections hints and answers for February 16: Tips to solve 'Connections' #616. No, Planned Parenthood's Instagram wasn't hacked SpaceX is so close to turning its rocket headquarters into an actual city Google Maps is adding weather incident reporting Best Presidents' Day deal: Save $130 on Samsung Galaxy Buds2 Pro Best Max deals and bundles: Best streaming deals in February 2025 NYT Connections Sports Edition hints and answers for February 15: Tips to solve Connections #145 Tim Cook teases Apple launch next week, which might be the new iPhone SE 'The White Lotus' Season 3: Why is Tanya's husband Greg at the hotel? Ruggable Presidents' Day Sale 2025 Golden State Warriors vs. Houston Rockets 2025 livestream: Watch NBA online What's new to streaming this week? (Feb. 14, 2025) Think this space station and moon photo is AI? Meet the photographer. Best Disney+ deals and bundles: Best streaming deals in February 2025 Best Presidents' Day deal: Save $150 on Garmin Forerunner 955
1.3921s , 10139.1171875 kb
Copyright © 2025 Powered by 【Request Movies】,Exquisite Information Network